The Operating System Laboratory of the School of Computer Science at Peking University has been engaged in research on operating system security in ubiquitous computing environments for a long time. Since the first half of 2023, the laboratory has made a series of breakthroughs in provenance analysis, attack detection and protection, AI system security, etc. A total of six papers have been accepted by multiple top international academic conferences/journals in the field of computer security such as S&P, CCS (2 papers), Usenix Security, NDSS and TDSC. The supervising teacher team includes Assistant Professor Ding Li, Professor Yao Guo and Professor Xiangqun Chen.
The following is a brief introduction to the content of these papers:
1. Resource Isolation Required for Auditing Systems: A Systematic Study on Super Producer Threat to System Auditing and Its Mitigation
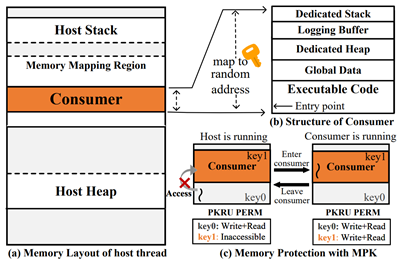
(a) The memory layout of the host thread, (b) the consumer for log processing and (c) the consumer is protected by MPK
System auditing is a key technology for detecting advanced persistent threat (APT) attacks. However, attackers may attempt to disrupt the auditing framework to hide their malicious activities. The paper "Auditing Frameworks Need Resource Isolation: A Systematic Study on Super Producer Threat to System Auditing and Its Mitigation" (Usenix Security 2023) found that existing audit frameworks face threats from super producers - processes that generate large amounts of logs - which can cause audit frameworks to fail (log loss) or even bring down entire systems. Through analysis, it was discovered that one major reason for this threat is that centralized architecture used by current audit frameworks lacks data isolation. To address this issue, a new type of audit framework called NODROP was proposed using threadlet-based architecture design to isolate system call logs generated by different processes. Evaluation shows that under different hardware configurations NODROP can ensure log integrity while only increasing application overhead compared with Vanilla Linux by 6.58%, and reducing application overhead by 6.30% compared with the most advanced commercial audit framework Sysdig.
The first author of this paper is Peng Jiang, a Ph.D. student in the School of Computer Science (supervised by Professor Xiangqun Chen), and the corresponding authors are Assistant Professor Ding Li, Professor Yao Guo, and co-authors include Professor Xiangqun Chen from Peking University, Dr. Yuxin Ren from Huawei (Peking University alumnus).
2. Security Research on Deep Learning Models under Trusted Execution Environment Protection
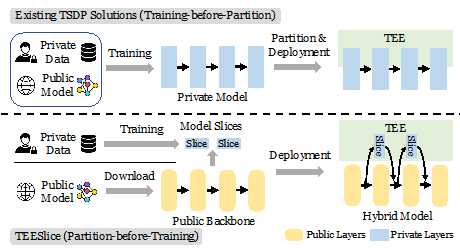
TEESlice uses a "partition-first training-later" strategy different from existing methods.
In recent years, large-scale deployment of deep learning models has brought new challenges to model security: device owners can obtain white-box information about deep learning models. Attackers can use this information for model stealing attacks and membership inference attacks. To protect the privacy of on-device models, developers have proposed various model partitioning methods based on trusted execution environments (TEEs). The paper "No Privacy Left Outside: On the (In-)Security of TEE-Shielded DNN Partition for On-Device ML" (S&P 2024) conducted a comprehensive security evaluation of existing model partitioning schemes using multiple settings and found that existing methods still leak a lot of privacy information when facing model stealing attacks or membership inference attacks. Based on these limitations, a new type of model partitioning method called TEESlice was proposed which uses a novel "partition-first training-later" strategy to achieve isolation between privacy parameters and non-privacy parameters. Experimental results show that compared with protecting all models inside TEEs, TEESlice can reduce latency overhead by more than ten times without sacrificing security.
The first author of this paper is Ziqi Zhang (supervised by Professor Chen Xiangqun, now a postdoctoral fellow at Peking University), and the corresponding authors are Professor Yao Guo and Assistant Professor Ding Li. Co-authors include Professor Xiangqun Chen from Peking University, Chen Gong, Yifeng Cai, Yuan-yuan Yuan from Hong Kong University of Science and Technology, Bingyan Liu from Beijing University of Posts and Telecommunications.
3. NodLink: An Online System for Fine-Grained APT Attack Detection and Investigation
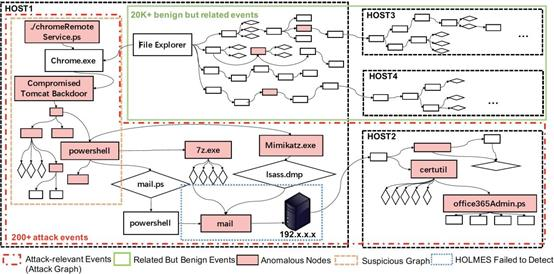
APT29's traceability diagram example: NodLink can accurately locate attacks with traceability diagrams of about 200 nodes.
Advanced Persistent Threat (APT) attacks have been a persistent problem for enterprises, causing significant economic losses. To address these attacks, researchers propose modeling system entities and their dependencies using trace graphs to capture the complex and covert scenarios of APT attacks. There is an urgent need for an online trace detection system that can detect and investigate APT attacks under time constraints and limited resources to accelerate attack detection and reduce economic losses. The paper "NodLink: An Online System for Fine-Grained APT Attack Detection and Investigation" (NDSS 2024) designs and implements NodLink, the first online detection system that maintains high detection accuracy without sacrificing granularity in detecting APT attacks. The process of detecting APT attacks in the online trace detection system can be modeled as a Steiner tree problem (STP). The paper proposes a novel memory caching design, an efficient attack filtering method, and a new STP approximation algorithm that is more efficient than traditional algorithms while maintaining the same complexity in detecting APT attacks. NodLink was evaluated in production environments, with experimental results showing that it achieves higher detection accuracy with the same or higher throughput compared to two state-of-the-art online trace analysis systems.
The first author of this paper is Shaofei Li, a Ph.D. student from the School of Computer Science (supervised by Professor Xiangqun Chen), while Ding Li serves as the corresponding author. Collaborators include Professor Yao Guo from Peking University, Professor Xiangqun Chen from Peking University, as well as researchers from Huazhong University of Science & Technology and Sangfor Technologies.
4. SymGX: Detecting Cross-boundary Pointer Vulnerabilities of SGX Applications via Static Symbolic Execution
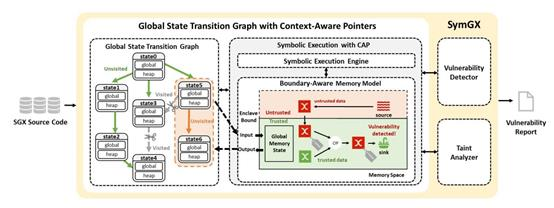
SYMGX Architecture
Intel Software Guard Extensions (SGX) provides hardware-based memory encryption, which has shown significant effectiveness in protecting critical data. Recently, symbol-execution-based techniques have revealed that SGX applications are vulnerable to memory corruption attacks. However, existing methods only focus on conventional memory corruption vulnerabilities in SGX applications and ignore a critical type of vulnerability unique to SGX: cross-boundary pointer vulnerabilities. These vulnerabilities are crucial for SGX applications because they heavily rely on pointers to exchange data between trusted memory and untrusted environments. Unfortunately, existing symbolic execution methods lack an SGX-specific analysis model that can handle three features unique to SGX application execution: multi-entry arbitrary order execution, stateful execution, and context-aware pointers. Therefore, these methods cannot effectively detect cross-boundary pointer vulnerabilities. To address these issues, the paper "SymGX: Detecting Cross-boundary Pointer Vulnerabilities of SGX Applications via Static Symbolic Execution" (CCS 2023) proposes a new analysis model GSTG-CAP that can simulate the execution of an SGX application while retaining its behavioral attributes to drive symbolic execution for vulnerability detection. Based on GSTG-CAP, a new symbol-execution-based vulnerability detector SYMGX is constructed to detect cross-boundary pointer vulnerabilities. Evaluation results show that SYMGX discovered 30 zero-day vulnerabilities in 14 open-source projects with three confirmed by developers. SYMGX outperforms two advanced symbolic-execution-based vulnerability detection tools COIN and TeeRex in terms of effectiveness, efficiency and accuracy.
The first author of this paper is Yuanpeng Wang from the School of Computer Science (supervised by Professor Yao Guo), while Professor Yao Guo and Ding Li serve as corresponding authors. Collaborators include Professor Xiangqun Chen from Peking University.
5. Efficient Memory Isolation for Domain-based WASM Applications
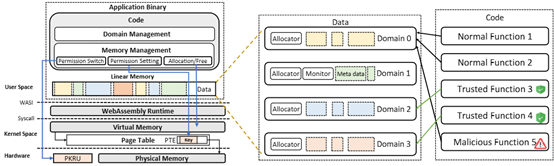
WebAssembly runtime linear memory domain isolation model
Memory corruption vulnerabilities in WebAssembly can cause more serious consequences than native applications. Therefore, we introduced PKUWA, the first WebAssembly runtime with memory isolation capabilities. We use MPK hardware for efficient memory protection in WebAssembly. However, MPK and WebAssembly have different memory models: MPK protects virtual memory pages while WebAssembly uses linear memory without pages. Mapping the MPK API to WebAssembly results in memory inflation and low efficiency. To solve this problem, the paper "Put Your Memory in Order: Efficient Domain-based Memory Isolation for WASM Applications" (CCS 2023) proposes DILM, which protects linear memory at a function-level granularity. We implemented DILM into the official WebAssembly runtime to build PKUWA. Our evaluation shows that PKUWA can prevent memory corruption with an average overhead of 1.77%, and the cost of memory is negligible.
The first author of this paper is Hanwen Lei, a Ph.D. student from the School of Computer Science (supervised by Professor Yao Guo), and the corresponding authors are Professor Yao Guo and Assistant Professor Ding Li; co-authors include Professor Xiangqun Chen, Ziqi Zhang, Shaokun Zhang, Peng Jiang, Zhineng Zhong, and Ningyu He.
6. Detecting Malicious Websites from System Provenance Analysis Perspective
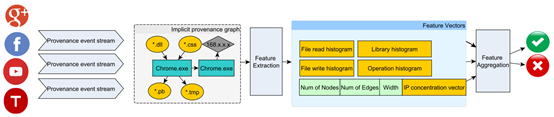
ProvWeb Architecture
Malicious websites are considered one of the biggest threats in modern internet. Traditional detection techniques usually rely on URL blacklists or static and dynamic code analysis, which have significant limitations in terms of detection effectiveness and deployment. In order to effectively detect malicious websites, the paper "Detecting Malicious Websites from the Perspective of System Provenance Analysis" (IEEE TDSC) studies them for the first time from the perspective of system provenance analysis. The study conducts comprehensive feature engineering research on system provenance data for thousands of normal and malicious websites. Eight useful detection features were discovered during this research. Based on these eight provenance data features, ProvWeb, a new non-intrusive real-time tool for detecting malicious websites was proposed. In evaluation, ProvWeb achieved F1 scores ranging from 93.7% to 99.7% for four combinations of browsers and operating systems (Windows Chrome, Windows Firefox, Linux Chrome, Linux Firefox). This result also confirms that features found in provenance graphs can effectively detect malicious websites.
The first author of this paper is Peng Jiang, a Ph.D. student from the School of Computer Science (supervised by Professor Xiangqun Chen), and the corresponding author is Assistant Professor Ding Li; co-authors include Professor Xiangqun Chen, Professor Yao Guo, Jifan Xiao, Hongyi Yu, and Yu Bai.
The relevant work has been supported by the National Key R&D Program, the Ministry of Science and Technology's "2030" New Generation Artificial Intelligence Special Project, the National Natural Science Foundation's special key project, and the National Natural Science Foundation's general project.
In the field of security, four major international conferences (S&P, CCS, Usenix Security, NDSS) accept about 100-200 papers each year with an acceptance rate generally not exceeding 20%. In recent years, Peking University Operating System Laboratory has carried out a series of cutting-edge research work in the field of ubiquitous computing system security. It is expected to make further important contributions to Peking University's development in computer security.
